ARC, or Authenticated Received Chain, is a standard created in 2016 to help improve how DKIM and SPF results are passed from one mail server to the next during forwarding. When messages are passed to intermediaries like mailing lists or email account forwarding DKIM and SPF can break. ARC aims to fix this.
In simpler terms, the Authenticated Received chain can be termed as a sequence of verification for email messages that enables each entity that handles the messages to effectively see all the entities that previously handled it.
Situations in Which ARC Can Help
- Mailing Lists
As a member of a mailing list, you have the power to send messages to all members in the list at one go by addressing the mailing list itself. The receiving address then subsequently forwards your message to all list members. In the current situation, DMARC fails to validate these types of messages and the authentication fails even though the email has been sent from a legitimate source! This is because SPF breaks when a message is forwarded. As the mailing list often goes on to incorporate extra information in the email body, the DKIM signature can also be invalidated due to changes in the email content.
- Forwarding Messages
When there is an indirect mail flow, such as you are receiving an email from an intermediate server and not directly from the sending server as in the case of forwarded messages, SPF breaks and your email will automatically fail DMARC authentication. Some forwarders also alter the email content which is why the DKIM signatures also get invalidated.
ARC validation
In the situations listed above, the forwarders had initially received emails that had been validated against DMARC setup, from an authorized source. Authenticated Received Chain is developed as a specification that allows the Authentication-Results header to be passed on to the next ‘hop’ in the line of the message delivery.
In case of a forwarded message, when the receiver’s email server receives a message that had failed DMARC authentication, it tries to validate the email for a second time, against the provided Authenticated Received Chain for the email by extracting the ARC Authentication-Results of the initial hop, to check whether it was validated to be legitimate before the intermediary server forwarded it to the receiving server.
On the basis of the information extracted, the receiver decides whether to allow the ARC results to override the DMARC policy, thereby passing the email as authentic and valid and allowing it to be delivered normally into the receiver’s inbox.
With ARC implementation, the receiver can effectively authenticate the email with the help of the following information:
- The authentication results as witnessed by the intermediate server, along with the entire history of SPF and DKIM validation results in the initial hop.
- Necessary information to authenticate the sent data.
- Information to link the sent signature to the intermediary server so that the email gets validated in the receiving server even if the intermediary alters the content, as long as they forward a new and valid DKIM signature.
Implementation of Authenticated Received Chain
ARC defines three new mail headers:
- ARC-Authentication-Results (AAR): First among the mail headers is the AAR that encapsulates the authentication results such as SPF, DKIM, and DMARC.
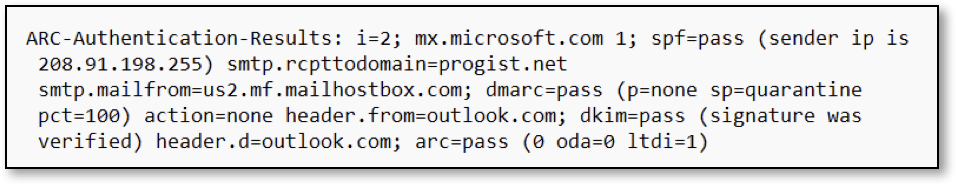
- ARC-Seal (AS) – AS is a simpler version of a DKIM signature, that contains information on authentication header results, and ARC signature.

- ARC-Message-Signature (AMS) – AMS is also similar to a DKIM signature, which takes an image of the message header which incorporates everything apart from ARC-Seal headers such as the To: and From: fields, subject, and the entire body of the message.
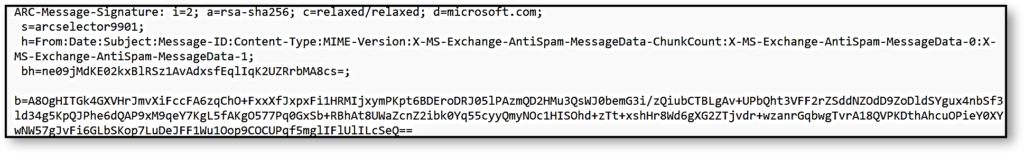
Finally, to validate the Authenticated Received Chain and find out whether a forwarded message is legitimate or not, the receiver validates the chain or ARC Seal-headers and the newest ARC-Message-Signature. If in case the DMARC ARC headers have been altered in any way the email consequently fails DKIM authentication. However, if all mail servers involved in the transmission of the message correctly sign and transmit ARC then the email preserves the DKIM authentication results, and passes DMARC authentication, resulting in the successful delivery of the message in the receiver’s inbox.
